The year 2017 is becoming a memorable one thanks to widespread attacks such as Wanacrypt and NotPetya, which locked down your files then used your computer to spread the malware like wildfire. Hackers are using more advanced techniques to ensure their attacks cause more damage to systems on a wider scale. But just because hackers are getting smarter doesn’t mean that users necessarily have to. We just have to be consistent and conscientious about how we maintain our PCs. In this article, you’ll find everything you need to do just that.
Basic Tips to Keep Your Computer Safe from Ransomware
In the same way that you cannot drive a car without risk, you can’t use a computer without a certain amount of risk. The fact that you are reading this blog post means that you’ve decided to accept that risk. The question is: How will you manage that risk? First, let’s identify the threat.
Keep your operating system, applications, and anti-virus up to dateBack up, back up, back up—use something like BackBlaze or CrashPlan that lets you restore a previous version of your data from a certain date, in case your synced files get encrypted too.Use a different strong password for every site (not the same one over and over)
One of the dangers of using a computer—particularly one connected to the internet—is that you may become infected by ransomware. Ransomware is a virus or malware that encrypts the files on your computer, which prevents you from accessing them unless you pay a fee to “buy back” your data with a decryption key. Of course, there’s no guarantee that you’ll actually get your data back by paying the ransom—the mechanisms for delivering the decryption key were quickly shut down for both the WannaCry and Petya-variant attacks in 2017. The NotPetya attack had another insidious twist to it: it also stole login credentials stored on your computer and transmitted them back to the hacker. And, as with all viruses, infected hosts quickly spread the virus to other computers. So, the impacts of getting infected by ransomware are (1) loss of personal data, (2) loss of money, if you pay the ransom, (3) compromise of your login credentials, and (4) spreading the infection. There are two main ways to manage this risk: You can reduce your risk by making your computer less vulnerable to ransomware attacks. And you can mitigate your risk by lessening the impact in the event that you do get infected. Which risk management strategy should you employ? That’s right—both! First, let’s tackle the risk reduction aspect.
Reducing Your Risk of Ransomware Infection
Ransomware attacks are getting more and more sophisticated, but for the everyday user, your response remains the same: keep your operating system up to date and maintain good computer hygiene. In a nutshell, install updates as soon as they are released and be careful where you click and what you download. Here’s your ransomware risk reduction checklist:
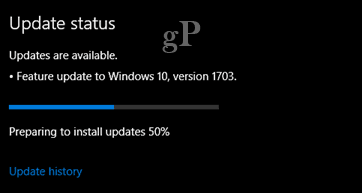
Install Windows Updates
Security patches may not be as exciting as Windows feature updates, but they are just as important (if not more). The team at Microsoft works hard to identify threats and eliminate vulnerabilities. Your job is simply to install the fixes as soon as they are available. Case in point: the security update that protects Windows computers from the WannaCrypt attack was released way back in March 2017. Another example: The initial version of Windows 10 software launched in 2015 is already considered outdated. A proof of concept code demonstrated an attack that was able to take down the initial releases (1507 and 1511), but the Anniversary Update (version 1607) held on strong. As soon as you hear about a security update, that’s when you should install it. Why? First of all, vulnerabilities are often known within the community before a fix is available. Secondly, hackers are always looking at updates then dismantling them to find clues for vulnerabilities that exist in older releases. When Microsoft launches these new updates, you need to embrace them right away. Sure, they are a small inconvenience to install, but it’s certainly less inconvenient than losing access to all your data.
Microsoft does an awesome job with releasing updates regularly and providing options to make installing Windows Updates less of a hassle. In the past, we have looked at ways to block Windows Updates, but this is bad advice in this day and age. To manually check, head to Settings > Update & security > Windows Update. Install those updates as soon as you can!
Install the Latest Antivirus Software and Definitions
If you use the built-in protection utility, Windows Defender Security Center (Now simply called: “Windows Security”)—which includes: Antivirus, Network Firewall, Device Health and Performance and other options—it does a fairly good job at protecting your system. Windows Update distributes definition updates automatically, too. Users who prefer a third-party solution need to ensure they keep their antivirus updated. This means, installing new versions as they become available, whether they are free or paid subscriptions. Installing the latest definitions is also important since antivirus signatures are key to preventing zero-day attacks.
Keep Those Applications Updated Too
If you have a lot of applications installed, any one of them could be an easy target or attack vector for ushering malicious code into the system. Keeping them updated will help reduce the chances of an attack. Regularly review your application list and remove Windows applications you don’t need. If this seems like too much of a chore, start downloading your applications from the Microsoft Store app, since they are properly vetted and packaged in a way they can’t be used to access parts of the system.
Remove Outdated and Obsolete Apps and Services
In the same way that old cars are unsafe on the highway, certain apps and services should be removed from your computer since they don’t meet current security standards. Our recent article delved into apps and services you need to stop using in greater detail. If you are using older unsupported technologies like QuickTime, make sure you remove them. There are some technologies like Java and Flash that are still supported but are not necessarily essential to have installed.
Properly Configure Microsoft Office Macro Settings
Sometimes, default settings can be enabled by your IT department if you are using apps like Office for better or worse. For instance, macros that help automate tasks in apps like Word, if enabled, could potentially be used to release infected code. If you have no need to use macros, make sure they are turned off in the Settings of your Office applications. Click File > Options, select the Trust Center tab, select Macro Settings then select Disable all macros with notification.
Mitigating Your Risk of Ransomware Infection
On the highway, defensive driving and obeying traffic laws will help you avoid a crash. If you are in a crash, airbags, seat belts, and the other safety features in your car will lessen your personal injury. Consider these ransomware risk mitigation tips your computer’s airbag in the event of an infection.
Don’t Pay the Ransom
Seeing that evil ransom note after you’ve been infected can bring on a sense of panic. But avoid instinctively reaching for your wallet. For one, the damage has already been done—your files have already been kidnapped. But more importantly, chances are, you won’t actually be able to get your data back by paying the ransom. And if you’ve done the remaining risk mitigation steps in this article, you won’t need to.
Backup, Backup, Backup
We keep saying it and we hope you are following the instructions to maintain a regular backup. It’s not as hard as it used to be. Windows 10 includes a number of options, from File History to System Image. These are not the only tools you should depend on; backing up to the cloud can be advantageous and makes restoration in the event of an attack seamless. There are a number of solutions out there such as Backblaze, CrashPlan, Microsoft’s own OneDrive, iCloud, Google Drive, and Dropbox. You can even spread your backups across services. For instance, I use Google Drive for Photos, OneDrive for Documents; I even keep multiple backs up of my personal data on multiple cloud platforms. It’s basically creating a backup of the backup. With a cloud and system image backup, if your machine becomes infected, all you need to do is reinstall Windows 10, restore and sync your data and your back in business. Mac users can follow our instructions for backing up their systems using the built-in Time Machine software. If you are running Linux, distributions such as Ubuntu, include a simple but handy backup tool, which you can find in the Settings app.
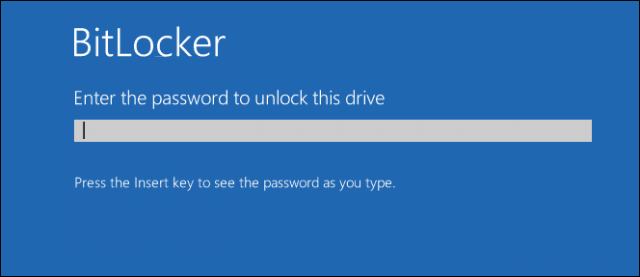
Encrypt Your Drives or Files
Cyber attacks are using encryption as part of their weaponry. You can fight fire with fire by encrypting your files or your entire hard drive. Our BitLocker guide shows the benefits of using encryption to keep your files safe from tampering. If you are not on Windows 10 Pro, this might be time to consider the upgrade to take advantage of it. Mac users can enable File Vault, which encrypts your Home folder.
A quick caveat: the security of your file and drive encryption depends on the security of your encryption keys. If a ransomware attack infects an account that has access to your files, it can still encrypt them. The problem is that the encryption happens in the background without you knowing it. If you’re logged in with your drives unlocked, then it’s game over. Encrypting your files can certainly help, especially if you encrypt certain drives or files and only unlock them when needed. But don’t let BitLocker or any other whole drive encryption lull you into a false sense of security when it comes to ransomware.
Secure Your BIOS
If you use a modern PC using the UEFI firmware, check to make sure Secure Boot is enabled. Sometimes it can be disabled for one reason or another, whether reinstalling Windows or making modifications to the firmware itself. Review our guide for steps on how to load your UEFI firmware interface, then check the security settings to ensure Secure Boot is enabled.
If Secure Boot is enabled, your computer won’t boot if your bootloader has been tampered with. This is a hallmark of some ransomware attacks. While this won’t prevent infection of your PC, it may prevent you from spreading the infection to others.
Change Passwords and Use 2FA
As mentioned above, some ransomware attacks will steal credentials as well as locking your files. To lessen the damage of this occurring, make sure you change your passwords frequently. Also, using different passwords for websites and logins is also important. Check out our password creation guide for tips. You can also use third-party services like LastPass or Bitwarden or 1Password to help with creating and managing your password. Using 2FA can greatly help with reducing the chances of an attack from happening. If you get a pop-up on your phone that someone from a foreign country is trying to log into your account and you are not in that location, you can safely take steps to protect your system.
Other Tips for Good Computer Hygiene
The tips above are your best bets for reducing and mitigating your risk of ransomware. If you do nothing else, take the steps described above. If you want extra credit and even more layers of security, consider the following:
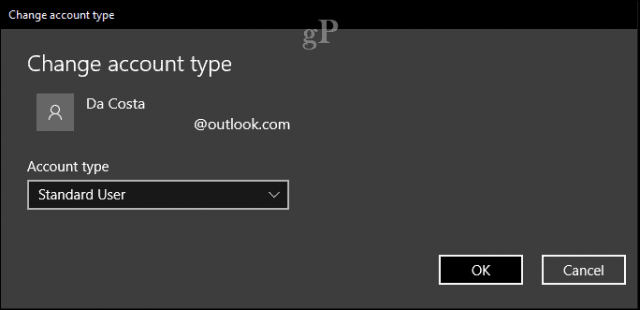
Set Up a Limited User Account for Daily Usage
Windows 10’s Standard Administrator Account privilege does a pretty good job preventing malicious code from easily executing and causing system-wide damage. On top of that, Microsoft’s own Edge browser is pretty solid when it comes to security by providing a virtualized environment, so things like drive-by downloads cannot easily execute code. A limited user account for daily usage can go even further. This account would be used for the most mundane activities: email, browsing the web, office productivity, listening to music, and viewing photos. When you need to perform system administrative-type activities like troubleshooting, installing new hardware or software, you can use the Standard Administrator account instead. It’s an extra layer of security users don’t realize you have in your arsenal.
Be Conscious of the Sites You are Visiting
The internet is vast and there are so many websites out there, it’s impossible to know what’s good or bad. Even the good ones can easily be compromised or host malicious code in elements like ad banners. So, users should be careful what they click or the links they open. Viral videos on social media websites are a particularly powerful way to get users to open sites they think might be harmless. Avoid them, if the video is not embedded in the social media page, forget it and move on. There are some pages on social media too, that use thumbnail images with a play icon—watch out for those.
Maintain a Throw-Away Email Address
It is recommended you don’t use your regular email address used to communicate with close family and friends for signing up and authenticating on certain websites. Malicious software will target your contacts as one of its first measures by sending booby-trapped emails with attachments under your account name. Recipients will unsuspectingly open emails without hesitation and become infected. Email remains a common vector for spreading malicious code. An unsuspecting email attachment could just be the booby trap that unleashes the bad code on your system. If you weren’t expecting an attached Word document from a colleague, send a quick message or give them a call just to confirm they did send it and get a quick synopsis to find out what it’s about. Also, consider using a quality encrypted email service like ProtonMail.
Go Offline
Worried that the Internet is full of malware? Then just don’t use the internet! “In 2017? Yeah right,” you’re probably thinking. But, it’s not such a ridiculous suggestion. If you are performing activities that don’t require an internet connection, you can keep the net turned off until you really need it. Using the Airplane Mode tab is a quick way to go offline without unplugging. In fact, if you suspect an attack might be in progress and you have multiple machines that could potentially become exposed, this might be the fastest way to do it before it spreads.
Conclusion
Tackling the threat of ransomware is a lot to think about, but it’s certainly worth the effort versus facing the red text on an ominous screen demanding $300 worth of Bitcoins to get your data back. Stay up to date on your operating system and application updates, don’t click on links in unsolicited emails or shady websites, and for your own sake, back up your data! Security experts are working hard to keep us safe—do your part by using the tools they give us. On that front, Microsoft is working on some advanced security enhancements for the next revision of Windows 10, called the Fall Creators Update. For example, Protected Folders is a new feature that keeps your personal files safe from applications that try to interfere with them in malicious ways. By default, your personal folder is protected, but you can add your own folders outside of these parameters. So, that’s definitely a reason you’ll want to upgrade to the next version of Windows 10.
There are drastic steps you can take such as using a mix of alternative operating system platforms like a Linux box or Chromebook, but these systems are not immune from the attacks either. You don’t want to go to an extent where using your PC feels you are entering the Matrix. Ransomware attacks are not entirely preventable, but these simple precautions, with a little common sense, can help you go long way towards protecting your systems and fellow users you keep in contact with. Have you ever been infected by ransomware? What did you do to recover? What do you do now to stay safe? Share with your fellow groovyPost readers in the comments! Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.
![]()